Mask dynamic secrets from GitHub Action's logs

2 min read | by Jordi Prats
GitHub will mask all the configured secrets from it's logs, but sometimes some secrets are retrieves from different sources (like AWS credentials, secrets fetched from other sources...) We don't want them to be stored as clear text in the GiHub's Actions logs, so we'll have to use add-mask to prevent it
To do so we'll use ::add-mask:: with the value we want to mask. For example:
echo "::add-mask::$SOME_SECRET_VAR"
Using this code the values of the SOME_SECRET_VAR will no longer be visible in the log from that point onwards with three stars. It is very important to make sure the variable is not print before adding the add-mask because otherwise it will be visible.
That's why you need to use a variable to mask the secret, if you mask the secret with a literal it will appear in the logs. For example:
name: test-add-mask
on: [push]
jobs:
release:
runs-on: ubuntu-latest
steps:
- run: |
echo '::add-mask::test'
echo This is a test
On the logs we would find the secret in the add-mask command:
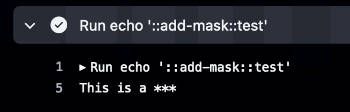
That's why we need to use a variable in order to mask the secret from the add-mask command.
Posted on 10/01/2023