-
Show current Kubernetes context in the menu bar
2 min read
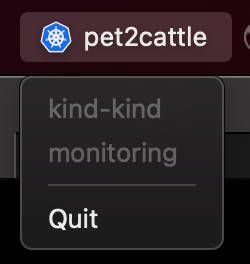
Some commands might be safe to execute while connected to some environments, but can definitely break stuff is applied to the wrong Kubernetes cluster. However, having to execute kubectl config current-context too ofter to make sure we are connected to the right cluster is no fun either.
With kubectx tray we can have a small icon on the tray bar to help us identify what's the current cluster.
30/11/2022
Read more... -
Kubernetes - Check with RBAC: Can I...?
2 min read

When configuring RBAC permissions we might want to make sure we are configuring them correctly by checking what an user (or ServiceAccount) can do. We can use kubectl auth can-i for this.
29/11/2022
Read more... -
OpenShift route TLS termination: edge, passthrough and reencrypt
2 min read

To be able to expose a service externally on OpenShift we can use the Route object. Generally speaking, Routes can be either secured or unsecured, in case we choose to use a secured route we can configured it to work in three different ways: edge, passthrough and reencrypt.
28/11/2022
Read more... -
Kubernetes: Pod failinig with: exec user process caused "exec format error"
2 min read

A Pod can fail to run with the following error:
standard_init_linux.go:178: exec user process caused "exec format error"24/11/2022
Read more... -
OPA Gatekeeper: Globally restrict it's scope to selected namespaces
2 min read

To prevent OPA Gatekeeper to apply rules to some namespaces we can add exclusions at the rule level but this can be very inconvenient since we would need to add it to every single rule. A change on these exclusion list can be a pain as well.
We can configure the ValidatingWebhookConfiguration to restrict it globally to namespaces that have a some label.
23/11/2022
Read more... -
Run commands impersonating another user or ServiceAccount
2 min read

To be able to test permissions it can be convenient to have our own user being able to impersonate other users (and ServiceAccounts as well). To do we we'll have to use the impersonate verb as follows:
- apiGroups: [""] resources: ["users", "groups", "serviceaccounts"] verbs: ["impersonate"]22/11/2022
Read more... -
Kubernetes: Generate a CRD definition from an object
2 min read

Let's face it, manually define a openAPIV3Schema definition is no easy task, so why not automating it? We can use this online CRD generator to be able to create it's definition from one sample object
21/11/2022
Read more... -
Exclude certain namespaces from a OPA gatekeeper rule
2 min read

While some policies can be safely applied to all the namespaces of a cluster, some other can become problematic since they can interfere with the normal operations of certain controllers. When we create a constrain rule we can exclude some namespaces using the spec.match.excludedNamespaces attribute
18/11/2022
Read more... -
Patch an existing manifest to delete an object using Kustomize
2 min read

Sometimes we'll need to delete a specific resource from an existing manifest. It can be as simple as moving the resource around, but if we do not control the source manifest it might not be an option: In this scenario we can delete the resource using a patch
17/11/2022
Read more... -
Kubernetes: Configure privilege escalation using the escalate and bind verbs
2 min read

The RBAC API prevents privilege escalation at the API level when creating or updating ClusterRole, ClusterRoleBinding, Role and RoleBinding. However, we can configure it to allow privilege escalation using the escalate and bind verbs.
15/11/2022
Read more...